|
Related Links
Surveillance Self-Defense Guide
How NSA’s Domestic Spying Program Works
How the NSA's Domestic Spying Program Works
Timeline of NSA Domestic Spying
The State Secrets Privilege
Eavesdropping 101
Warrantless Wiretapping Was Far More Involved Than Previously Known: Stellar Wind
House Extends Warrantless Email Snooping for 5 More Years - FISA
At&T's Role in Surveillance
Supreme Court Terminates Warrantless Electronic Spying Case
PBS Interview with AT&T's Mark Klein about NSA Data Intercepts
Behind the legal fight over NSA's "Stellar Wind" surveillance
How the U.S. Became Switchboard to the World
Is the NSA spying on U.S. Internet traffic?
NSA Domestic Interception Points
NARUS - The Ultimate Net Monitoring Tool
Uncovering Stingrays, a Troubling New Location Tracking Device
Ragtime: Code name of NSA's Secret Domestic Intelligence Program Revealed
A hidden world, growing beyond control
The Internet is a surveillance state
Who Has Your Back? Which companies help protect your data from the government?
Are all telephone calls recorded and accessible to the US government?
After the Tragedy in Boston, More Government Surveillance is Not the Answer
Kafka, Meet Orwell: Peek Behind the Scenes of the Modern Surveillance State
President Foreshadows New Internet Surveillance Proposal During National Security Speech
Sources: NSA sucks in data from 50 companies
Meet the Boundless Informant, the NSA's Data Overview Tool
Why the NSA's Secret Online Surveillance Should Scare You
Leaked NSA Doc Says It Can Collect And Keep Your Encrypted Data As Long As It Takes To Crack It
How the NSA's Surveillance Procedures Threaten Americans' Privacy
NSA Inspector General report on email and internet data collection under Stellar Wind
FAQ: What You Need to Know About the NSA's Surveillance Programs
James Clapper is Still Lying to America
Why "we only spy on foreigners" doesn't work any more for the NSA
Snowden Seen as Whistle-Blower by Majority in New Poll
The Creepy, Long-Standing Practice of Undersea Cable Tapping
Jimmy Carter Defends Edward Snowden, Says NSA Spying Has Compromised Nation's Democracy
Exclusive: U.S. directs agents to cover up program used to investigate Americans
Former NSA Chief on Latest Leaked Dragnet Spy Program: It's Real, and It's Spectacular
XKeyscore presentation from 2008 - read in full
NSA Said to Search Content of Messages to and From US
NSA broke privacy rules thousands of times per year, audit finds
ODNI / NSA Conference call "on background" to NSA surveillance - 8/21/2013
NSA misrepresented scope of data collection to secret court
Revealed: The NSA's Secret Campaign to Crack, Undermine Internet Security
Did NSA Put a Secret Backdoor in New Encryption Standard?
Microsoft and Yahoo voice alarm over NSA's assault on internet encryption
This is the crypto standard that the NSA sabotaged
RSA Tells Its Developer Customers: Stop Using NSA-Linked Algorithm Dual EC DRBG
Dianne Feinstein Accidentally Confirms That NSA Tapped The Internet Backbone
How the NSA Could Hack (Almost) Any Browser
Surveillance Industry Index
How does the NSA break SSL?
5 Shocking New Revelations on NSA Cellphone Tracking
Yet Another Surveillance Tool in FBI Hands. But How Are They Using It?
The US government doesn't want you to know how the cops are tracking you
How One New Drone Tech Finally Allows All-Seeing Surveillance
Meet the shadowy tech brokers that deliver your data to the NSA
New police radars can 'see' inside homes
The federal government could be taking pictures of you in your car
Thought bulk data collection was gone? Think again
Turns Out Police Stingray Spy Tools Can Indeed Record Calls
Everything We Know About How the FBI Hacks People
Secret Text in Senate Bill Would Give FBI Warrantless Access to Email Records
Surveillance Industry Index
Long-Secret Stingray Manuals Detail How Police Can Spy on Phones
Tech firm tries to pull back curtain on surveillance efforts in Washington
Technology and Shifting Privacy Expectations
What Does It Really Take To Track A Million Cell Phones?
The Senate Intelligence Committee 702 Bill Is a Domestic Spying Bill
A Guide to Law Enforcement Spying Technology
How to hide from the AI surveillance state with a color printout
The Terrifying Potential of the 5G Network
The Dawn of Robot Surveillance: AI, Video Analytics, and Privacy
The Intelligence Community is Exploring Long-Range Biometric Identification
High-Tech Tools Police Can Use to Surveil Protesters
|

Surveillance Techniques: How Your Data Becomes Our DataIn 2001, NSA published the secret "Transition 2001" report defining our strategy for the 21st century. No longer could we simply access analog communications using conventional means, the new digital world of globally-networked encrypted communications required a dramatic change to our surveillance strategy: NSA would need to "live on the network". We've turned our nation's Internet and telecommunications companies into collection partners by installing filters in their facilities, serving them with secret court orders, building back doors into
their software and acquiring keys to break their encryption.
Backdoor SearchesSection 702 of the Foreign Intelligence Surveillance Act (FISA) provides us with a bonanza of "incidental" data collected from ordinary Americans communicating with foreigners targeted by this sweeping law. This convenient loophole allows us to peruse this database in our never-ending search for the elusive "needle in a haystack".
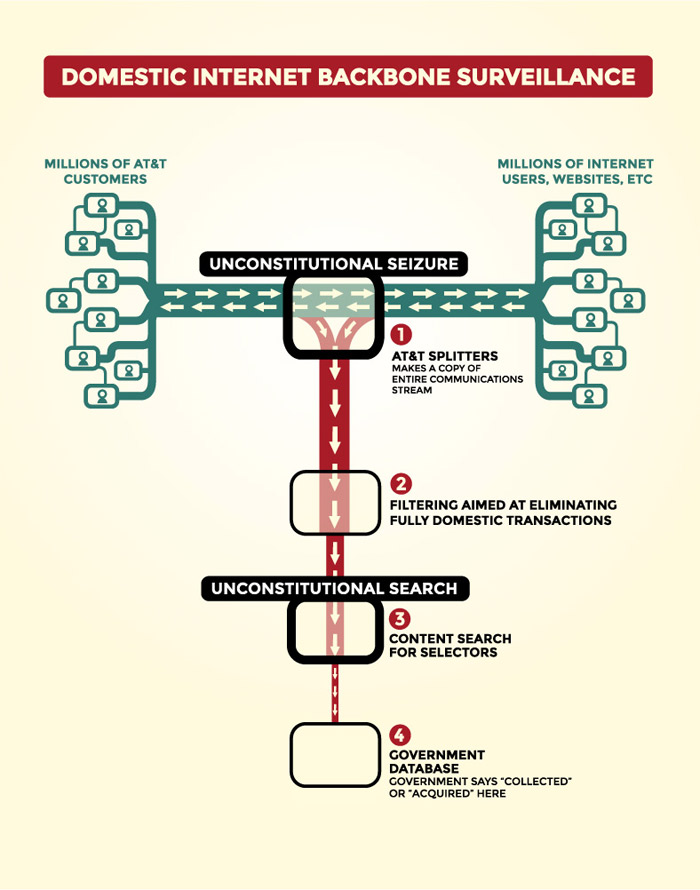
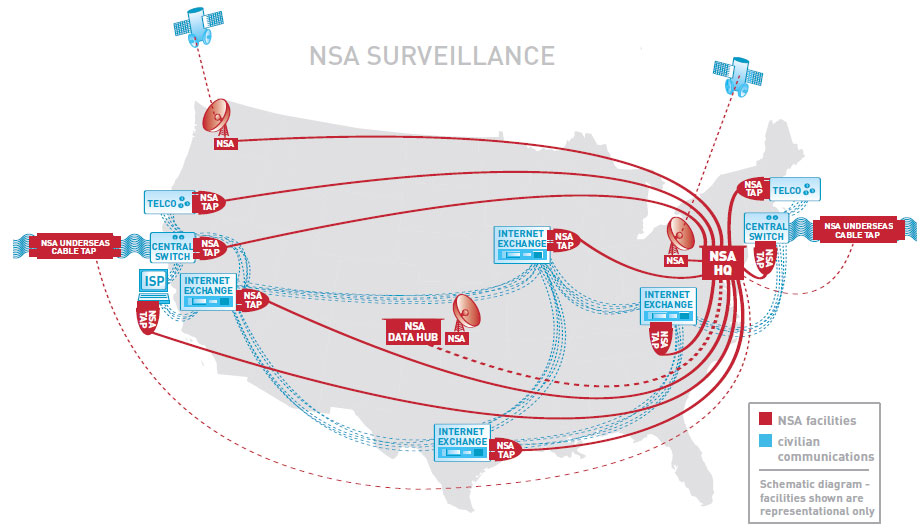
Our Domestic Intercept StationsNSA technicians have installed intercept stations at key junction points, or switches, throughout the country. These switches are located in large windowless buildings owned by the major telecommunication companies and control the domestic internet traffic flow across the nation.
A fiber optic splitter is placed on the incoming communication lines and routes the traffic to an NSA intercept station for processing.
Bulk Collection of U.S. Citizens' Phone RecordsIn the past, we used our close partnership with the FBI to collect bulk telephone records on an ongoing basis using a Top Secret order from the Foreign
Intelligence Surveillance Court (FISC). The metadata we collected from this program gave us information about what communications you sent and received, who you talked to, where you were when you talked to them, the lengths of your conversations, and what kind of device you
were using.
Cellphone TrackingOur bulk cellphone location tracking program captures almost 5 billion records a day and feeds into a massive 27 terabyte database storing information about the locations of a hundred million devices. By tapping into the cables that connect the mobile networks globally and working with our corporate partners to install intercept equipment, we can apply mathematical techniques that enable our analysts to map cellphone owners' relationships by correlating their patterns of movement over time with thousands or millions of other phone users who cross their paths. This "Co-traveler" program allows us to look for unknown associates of known intelligence targets by tracking people whose movements intersect.
FBI Aviation Surveillance Operations (FBI Hawk Owl Project)An FBI fleet of over one hundred specially-modified Cessna planes equipped with sophisticated camera systems
in steerable mounts that can provide detailed video, night vision, and infrared thermal imaging quietly fly circular routes daily around many major U.S. cities tracking
targets and gathering intelligence.
Some of the planes use “augmented reality” software and sophisticated surveillance technology capable of tracking thousands of cellphones users.
FBI Aerial Surveillance in the Continental U.S.Zoom in and click on the red map markers to view images of the unusual flight patterns in the FBI's targeted areas. View the map in full-screen mode.
FBI Aerial Surveillance in Hawaii
S. 1595: Protecting Individuals From Mass Aerial Surveillance Act of 2015In June 2015, a Senate bill was introduced to "protect" our citizens from Mass Aerial Surveillance. We are happy to report that no action has been taken on this bill and we have every confidence that Congress will agree with us that mass surveillance "IS" protection for our citizens. You can track the progress of this ill-advised bill below.
Our Undersea Cable Tapping StrategyBy tapping into the worldwide network of undersea cables, our OAKSTAR, STORMBREW, BLARNEY and FAIRVIEW systems can process data as it flows across the internet. Each
system is responsible for different types of intercepted data. For example, the BLARNEY system gathers metadata describing who is speaking to whom and through which networks and devices.
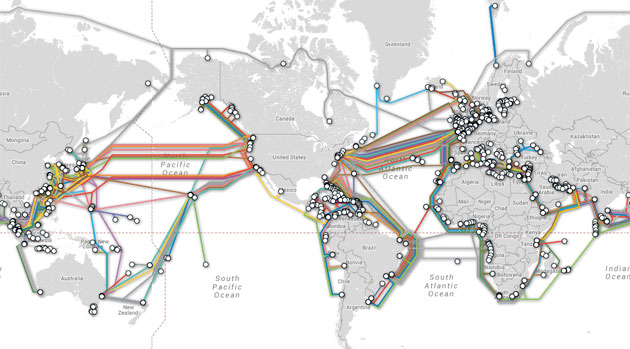 View an interactive map of worldwide undersea cables
View an interactive map of worldwide undersea cables
XKeyscore: Our Real-Time Internet Monitoring CapabilityAs data flows through our worldwide data collection points, the XKeyscore system indexes and stores this information in a rolling three-day buffer database containing all internet activity passing
through each collection site. XKeyscore is a massive distributed Linux cluster with over 700 servers distributed around the world.
Surveillance Data from Other SourcesIn addition to our own data collection activities, the Domestic Surveillance Directorate receives a constant flow of information from other sources. For more information about these sources, visit Our Partners page. |

| HOME |  |
YOUR DATA |  |
SURVEILLANCE TECHNIQUES |  |
OUR PARTNERS |  |
UTAH DATA CENTER |  |
JOBS |  |
ABOUT US |

 Domestic Surveillance Directorate
Domestic Surveillance Directorate