|
Related Links
NSA Buys Americansí Internet Data Without Warrants The Eternal Value of Privacy
Why Privacy Matters Even if You Have 'Nothing to Hide'
We Should All Have Something To Hide
How to Mess With Surveillance
Video: Why Care About the NSA?
How to Protect Your Privacy in the Age of NSA Surveillance
The NSA's Domestic Spying Program
NSA Whistleblower Says The Feds Are Gathering Data On Nearly Every US Citizen
U.S. Relaxes Limits on Use of Data in Terror Analysis
Pointing the US Surveillance Apparatus at the American People
NSA's Domestic Spying Grows As Agency Sweeps Up Data
Giving in to the Surveillance State
Total Information Awareness
DARPA's Information Awareness FBO Solicitation
U.S. Spies Buy Stake in Firm That Monitors Blogs, Tweets
Department of Homeland Security List of Keywords Used to Monitor Social Networking Sites
Attorney General Secretly Granted Government Ability to Develop and Store Dossiers on Innocent Americans
U.S. Spies Want to Find Terrorists in World of Warcraft
That's No Phone. That's My Tracker
The Real Scandal Surrounding the Petraeus Resignation
License plate readers: A useful tool for police comes with privacy concerns
New Tracking Frontier: Your License Plates
Big brother or better police work? New technology automatically runs license plates of everyone
Public Buses Across Country Quietly Adding Microphones to Record Passenger Conversations
CISPA permits police to do warrantless database searches
Biometric Database of All Adult Americans Hidden in Immigration Reform
No Warrant, No Problem: How The Government Can Still Get Your Digital Data
Revealed: NSA collecting phone records of millions of Americans daily
Telephone metadata and what it can tell the authorities about you
In the battle between privacy and security, security always wins
U.S. mining data from 9 leading Internet firms
Report: NSA targets credit card transactions
Lawmakers: Americans don't know how carefully the government is watching
Meet the contractors analyzing your private data
A Guardian guide to your metadata
Why you should worry about the NSA
NSA admits listening to U.S. phone calls without warrants
Skype's secret Project Chess reportedly helped NSA access customers' data
How the NSA is still harvesting your online data
In Secret, Court Vastly Broadens Powers of NSA
Revealed: how Microsoft handed the NSA access to encrypted messages
Video: Oliver Stone on NSA Spying
For NSA chief, terrorist threat drives passion to 'collect it all,' observers say
FISA court secrecy must end
You may already be a winner in NSA's "three-degrees" surveillance sweepstakes!
XKeyscore: NSA tool collects 'nearly everything a user does on the internet'
Unlocking the latest Wyden code: Does NSA operate a bulk domestic location tracking program?
Data Brokers Are Now Selling Your Car's Location For $10 Online
NSA can see 75% of U.S. Web messages
N.S.A. Foils Much Internet Encryption
How to remain secure against NSA surveillance
NSA Can Spy on Smart Phone Data
E-ZPasses Get Read All Over New York (Not Just At Toll Booths)
In ACLU lawsuit, scientist demolishes NSA's "It's just metadata" excuse
Silicon Valley wonders who is behind mystery NSA billboard
DHS - Facial Recognition Data Collection Project
NSA had test project to collect data on Americans' cellphone locations, director says
NSA Surveillance: a Guide to Staying Secure
What the Government Does with Americans' Data
Meet the "Dark Mail Alliance" Planning to Keep the NSA Out of Your Inbox
How Private is Your Online Search History?
Over one billion records in private license plate tracking database
LG Smart TVs logging USB filenames and viewing info to LG servers
Interactive: How police scoop up cellphone data
Blimplike surveillance craft set to deploy over Maryland heighten privacy concernsNew surveillance technology can track everyone in an area for several hours at a time
Why Online Tracking Is Getting Creepier
'You're the bomb!' Are you at risk from the anti-terrorism algorithms?
We know where youíve been: Ars acquires 4.6M license plate scans from the cops
Iris scanners can now identify us from 40 feet away
Facial recognition technology is everywhere. It may not be legal.
Automatic Face Recognition and Surveillance
Own a Vizio Smart TV? Itís Watching You
Youíre being secretly tracked with facial recognition, even in church
The Pentagonís secret pre-crime program to know your thoughts, predict your future
US intelligence chief: we might use the internet of things to spy on you
Upgrade Your iPhone Passcode to Defeat the FBIís Backdoor Strategy
What ISPs Can See
Your Conversation On The Bus Or Train May Be Recorded
Google Has Quietly Dropped Ban on Personally Identifiable Web Tracking
Terrorist or pedophile? This start-up says it can out secrets by analyzing faces
The FBI runs face recognition on 411 million photos, most of which are innocent Americans
Accessing Peopleís Browser History Is Almost Like Spying on Their Thoughts
Yahoo secretly scanned customer emails for U.S. intelligence
Your New Fridge Is Spying on You
Amazon reports large number of warrantless government demands for user info
Big Brother on wheels: Why your car company may know more about you than your spouse
Genome hackers show no oneís DNA is anonymous anymore
The Dangerous Junk Science of Vocal Risk Assessment
How your third cousinís ancestry DNA test could jeopardize your privacy
We Built a (Legal) Facial Recognition Machine for $60
Catholics in Iowa went to church. Steve Bannon tracked their phones
How to Turn Off Smart TV Snooping Features
Your Face Is Not Your Own
|

Your Data: If You Have Nothing to Hide, You Have Nothing to FearOur value is founded on a unique and deep understanding of risks, vulnerabilities, mitigations, and threats. Domestic Surveillance plays a vital role in our national security
by using advanced data mining systems to "connect the dots" to identify suspicious patterns.
Why We Collect Your DataIn the past, domestic law enforcement agencies collected data AFTER a suspect had been identified. This often resulted in lost intelligence and missed opportunities.
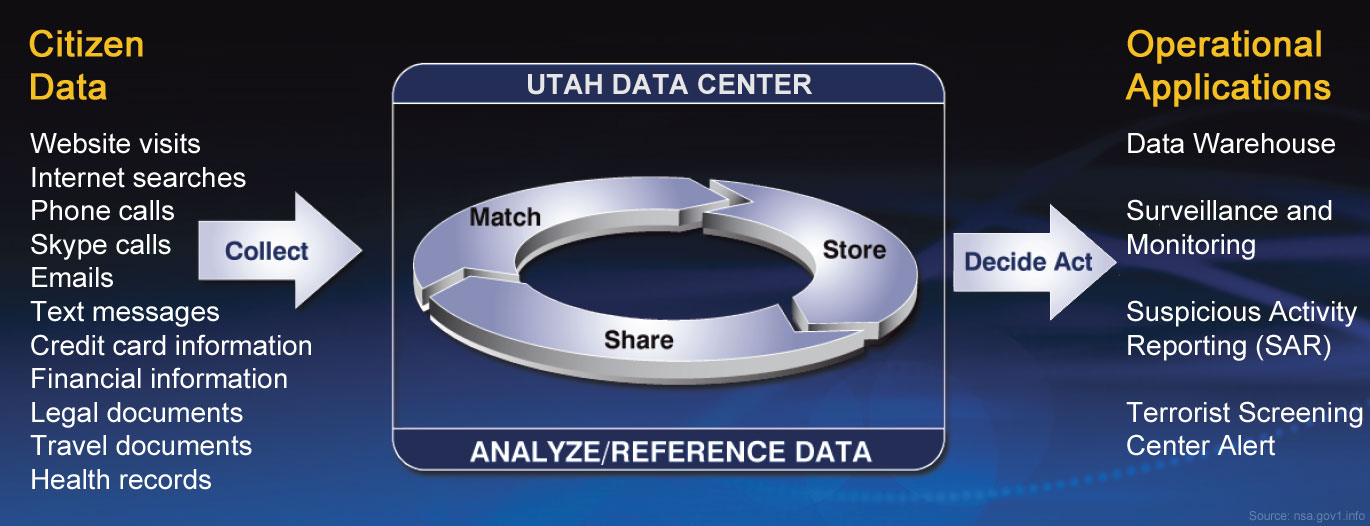
But what if data could be collected in advance, BEFORE the target was known? What if the mere act of collecting data could result in the identification of new targets? What Data We CollectEvery day, people leave a digital trail of electronic breadcrumbs as they go about their daily routine. They go to work using electronic fare cards; drive through intersections with traffic cameras; walk down the street past security cameras; surf the internet; pay for purchases with credit/debit cards; text or call their friends; and on and on. There is no way to predict in advance which crucial piece of data will be the key to revealing a potential plot. The standard operating procedure for the Domestic Surveillance Directorate is to "collect all available information from all available sources all the time, every time, always". In the spirit of openness and transparency, here is a partial list of current and planned future data collection targets:
How We Collect Your DataFor information on how we collect your data, visit our Surveillance Techniques page on this website. For information about our new state-of-the-art Surveillance Data Center, visit our Utah Data Center information page. 
How We Use Your DataWe treasure the U.S. Constitution and the rights it secures for all the people. In a world in which privacy has become illusory in so many areas of our lives,
the Domestic Surveillance Directorate maintains the highest standards of integrity and lawful action. Your private data is safely secured using our custom database
software called Cloudbase, which has fine-grained security to control access down to the cell level.
Threat Matrix ProcessingIncoming transactional data is analyzed against a continually evolving threat matrix and is assigned an action code. The vast majority of these transactions are routed directly to
a permanent static storage state. In fact, for most Americans, your data is never accessed or viewed by anyone within the US Government unless some future event triggers an inquiry.
We work closely with our partners in the Intelligence Community to ensure that your stored data is released only as a result of a "national security" request.
Continuity of GovernmentOur strong commitment to keeping the Nation safe includes an important role in maintaining the Continuity of Government. Since the early 1980s, the federal government has used its secret Main Core database to track dissidents and watchlisted Americans in the event of a national emergency. The roots of the Domestic Surveillance Directorate can, in fact, be traced back to the early days of this program. We are proud to continue this tradition by sharing our data with the modern-day COG program. Learn more about this.
 Future Uses of Domestic Intelligence DataIn 2006, the Intelligence Advanced Research Projects Activity (IARPA) was created to invest in high-risk, high-payoff classified programs uniquely designed to provide research and technical capabilities for the Intelligence Community. IARPA-funded researchers are currently studying novel ways of processing and analyzing the explosive growth of domestic data.
Why We Do What We Do

|

| HOME |  |
YOUR DATA |  |
SURVEILLANCE TECHNIQUES |  |
OUR PARTNERS |  |
UTAH DATA CENTER |  |
JOBS |  |
ABOUT US |

 Domestic Surveillance Directorate
Domestic Surveillance Directorate